Date Published July 9, 2020 - Last Updated December 10, 2020
On Monday, June 15, 2020, the US came under attack. A massive DDoS (Distributed Denial of Service) attack supposedly knocked out service from carriers such as T-Mobile and Verizon, and even social media platforms like Facebook and Twitch were affected. Anonymous tweeted about it, Congressional members railed against it, and various media outlets helped spread origin theories. The problem? It wasn’t true. The truth was much more mundane: a simple fiber failure.
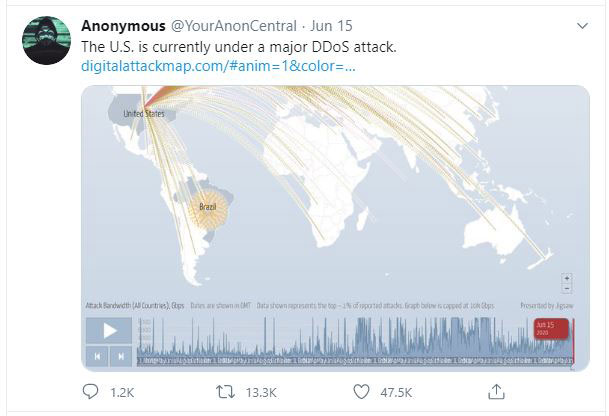
If so many people can get worked up about mere speculation, what chance do corporations and the IT departments that support them have to combat this misinformation, especially in the “next normal” where, for the time being, it seems distributed will be the new normal. To understand this, we need to understand the mechanisms of delivery and the importance of context in the propagation of misinformation. We can then focus on how ITSM departments can help.
Mechanisms
Without transmission, information dies. This isn’t some philosophical statement or meta-analysis of the nature of an autonomous revolution. It’s just the truth. If information cannot be passed along then it will eventually cease to exist. Transmission could be naturally occurring, a la the passage of genes from generation to generation, but it could also be manufactured or technological, a la bits and bytes going across a network in the form of an email, web page access, or Tweet.
While the speed and dispersion of the latter presents many benefits—the cloud, x-as-as-service, devices three times the total population of the world connected to IP networks by 2023—there are obvious tradeoffs. For one, there’s no easy way to verify prior to something going viral—just see the DDoS example I opened with. Even if we could check at that speed, there are fewer “checkers” as well. In the news industry alone, there has been a 47% reduction between 2004 and 2018 in reporters, editors, photographers, etc. It’s also not just speed but volume as well. On average, 55 billion legitimate emails are sent per day, and nearly six times that in spam over the same period. Then there’s the human side of things. While perhaps not deliberate “misinformation,” human error accounted for 90% of data breaches in 2019.
Each of these mechanisms—speed, volume, and human error—have particular needs and mitigation techniques. However, before we can talk about responding to these, we need to first address the power of context.
Context
Dealing with context will be handled in the following section, but I wanted to spend a moment highlighting why it’s so important. If we look at the image at the supposed DDOS attack that was shared on social media, it would seem like a scene from War Games had just started. But without context, this image is misleading, and we should not make inferences on it. I’m guilty as well. When I first saw the image, my initial thought was, “Ummm...uh oh.” But then you pause, do your best to scope things out, and remember context. Without proper context, any information—even harmless or successfully transmitted information—can be misinterpreted.
A simple thought experiment can help illustrate this: is the number “1” big? The simple answer is no. There are a ton of numbers higher than 1 (basically every other positive). But there are also just as many numbers lower than 1 if we include decimals and negative numbers. What if we were starting from there and counting up? Suddenly one, our seemingly small number, is virtually unattainable. So, in order to understand any form of information, you need proper context.
IT Response: The Three Cs
So, now that we know some mechanisms that we want to focus on, and we know the importance of context, how can we better equip our ITSM departments to tackle these issues? Put simply, whatever you choose to do, whatever mitigation technique, software, or process you use, to be effective, they will all need to share the same three qualities: consistency, communication, and context.
Consistency. What do we mean by consistency, when we’re speaking of things that are, hopefully, inconsistent (we hope your organization is not getting breached every day...though it’s certainly getting attacked every day)? By consistency I mean known, understood processes. If something were to happen, do your users know the email confirming or denying is coming from you (say, the ITSM department) or on the IT security letterhead? Is the format of such communications consistent? Does it have proper visual cues to be prioritized accordingly? By understood, do your users know how to spot phishing attempts? When was the last time you checked? How do you verify your training adequately? Has this changed since many of us work from home, etc.?
Communication. Part of being consistent is being able to effectively communicate, but this is all the more important in heavily dispersed times (like many of us find ourselves in now) or in times where mitigation needs to be quick. In these times, do you have processes and platforms in place to reach whom you need to, and do your users have the same for you? Also, in the case of an event, there may be a surge in tickets coming to the service desk. While these will be helpful to track, they will also become a drain on your limited resources. Do you have a process in place to effectively communicate to your user base that you know of the issue, you can provide updates, but that you cannot respond to each individually (that is, if you can’t).
Context. Finally, with context are you, via your consistent processes and communications, providing the right context? When I first started working in security engineering, I was hyper-sensitive to every little bug, hack, or breach I found out about. I quickly researched it and dispersed the information to any developer, manager, user, etc. that I thought needed to know. The net net of this approach was that my communications became ineffective, because while true, they lacked the context to prioritize accordingly. Some things take time to learn, so please learn from my mistakes. Always, always, provide appropriate context. When it’s serious, it’s serious. When it sounds serious, it might just sound serious. Respond accordingly.
Moving Forward
In a dispersed workforce like the kind many businesses have been forced to adapt to, implementing the three Cs has become even more of a priority. The increased onset of actual security events (a la the unsuccessful DDoS attack that hit AWS earlier this year) coupled with misinformation about potential ones (seems to be the case above, so far) presents a perfect storm of risk and subpar mitigation techniques. Make sure you are utilizing your resources appropriately, but, however you are, make sure those processes and functions are consistent, easy to communicate, and always provide the right context.
The increased onset of actual security events coupled with misinformation about potential ones presents a perfect storm of risk.

Adam Rauh has been working in IT since 2005. Currently in the business intelligence and analytics space at Tableau, he spent over a decade working in IT operations focusing on ITSM, leadership, and infrastructure support. He is passionate about data analytics, security, and process frameworks and methodologies. He has spoken at, contributed to, or authored articles for a number of conferences, seminars, and user-groups across the US on a variety of subjects related to IT, data analytics, and public policy. He currently lives in Georgia. Connect with Adam on LinkedIn.