Date Published October 22, 2019 - Last Updated December 17, 2019
Right. So, if you’ve read past the title, you’ve probably already got a picture in your head. But before we start chucking barstools and beer mugs, let’s take a moment to get some perspective…
In the best of circumstances, asset management can seem like a daunting proposition, a practice that seeks to gather all the stuff and things in one place—the more, the better. From a purely financial perspective, assets contribute to value, so building, creating, and managing assets should be at the heart of any business organization.
However, every asset increases exposure, multiplied by vulnerabilities multiplied by threats (which increase as anything becomes more valuable). So, we can imagine that any practice of information security management might look to the ever-increasing attack vectors as a competing and contradicting driver. Partner this with industry and organizational standards and policies of governance that continue to grow in complexity, and well, fur and feathers are bound to fly.
Every asset increases exposure.

I’ll save the actual human aspect of this scenario for our presentation at Service Management World. Here, I’ll focus on the practices themselves, and how to integrate the seemingly competing drivers. I think there is a rather simple solution, ripped straight from the headlines of ITIL 4: when in doubt, rely on guiding principles. It is a theme so common sense-ical that no one can disagree with. Common ground. Common Themes. Common Value.
Look at asset management and IT security management as some sort of force diagram. I imagine the asset practice pushing outward, trying to expand, capture, gather in all directions all things IT, while security is constantly pushing inward to limit and control, with governance and standards providing rigid walls all around.
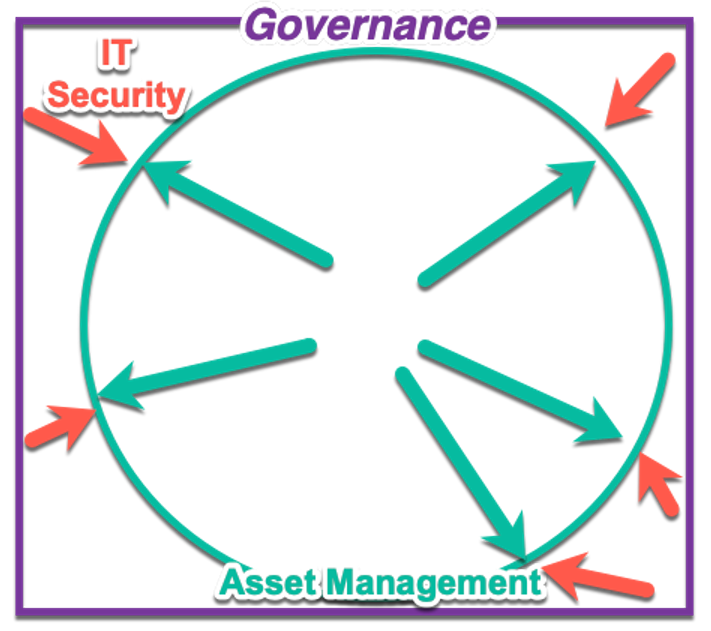
Here’s the thing: if we can keep our eye on the prize, opposing forces are the very thing that often drive and create value. The challenge, I think, is helping these practices keep the over-arching, over-riding guiding principles.
If we look at the middle ground between these forces, they can actually inform each other, benefit each other, and improve upon both practices. A matured and evolved asset management practice can identify the highest valued assets, thus providing crucial information for prioritizing IT security vulnerabilities and threats. An adept IT security management practice can provide crucial threat information that might impact not only asset depreciation and retirement plans and more. Governance structures like the Government Accounting Standards Board can provide guidance to inform upon things like the capitalization threshold for asset management, or, for that matter, crucial information about standardized and recognized vulnerabilities to IT security management, through the National Vulnerability Database (NVD).
Much like the opposing forces that produce diamonds from carbon, these two practices (asset management and security, buoyed by governance), can greatly increase the value of goods and services.
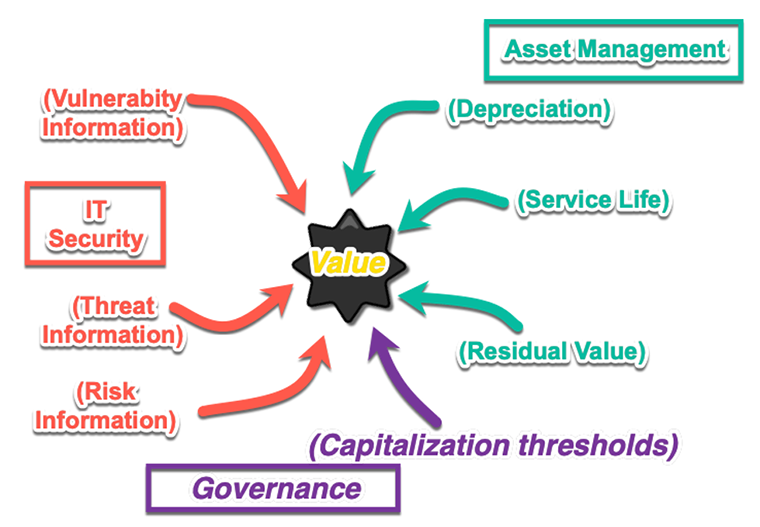
The challenge in each of these cases is remembering the central tenant: providing value. Much as ITIL 4 suggests value is co-created by customer and provider, the refinement of that value is determined by co-operation. If you’ve gotten past the bar stool throwing stage, then perhaps it’s time to look into some quick “Hows.”
- Asset management’s ever-expanding repository can be mined for prioritization in the practice of IT security:
- Ultimately, asset management is about resources and accounting and figuring out which assets are financially most sound and useful for the service provided.
- Core data, such as ROI, depreciation, retirement dates, residual can all be gathered and considered when prioritizing IT security operations.
- IT security’s external information about vulnerabilities and threats can be brought into the asset value consideration:
- Down times, patch and regression testing may all be considerations for asset end-of-life.
- Threat and vulnerability landscapes may be gathered to actually help make asset acquisition strategies (i.e., trends in exploitations suggest which hardware, operating systems, etc. might be favored or less favored).
- Governance can be used to create (or leverage existing industry or standard) policies for IT security, and asset management, giving better, more organized, more clear and concise risk values.
How you apply these components to work together depends upon the tools and toolsets you are using. But with any luck, your organization can start using these metrics to create value rather than broken bottles and chairs and windows.
Learn strategies for asset management, IT security, and governance at Service Management World!
Join us!
Sean McClean holds the designation of Master Trainer for one of the world's most innovative technology companies. Sean has been involved with training and implementation of IT service management tools and processes for governments, academia, and Fortune 500 companies for more than two decades. His expertise ranges from technical application implementation and development to IT process. Sean's certifications include ServiceNow CAD, CSA, CSI(IT), CSI(SIR), etc.; HP (AIS); ITIL (expert V2, V3); and Scrum Alliance (ScrumMaster). His contributions to the IT service management and training/facilitation fields span national and international conference presentations, articles, and reviews for organizations such as ZDNet, TFT, HDI SupportWorld, and more.